7 Commands for Windows CMD You Should Know
Command Prompt is still a strong Windows tool, and here are the most valuable CMD commands that every Windows user should be aware of.
The Command Prompt is gradually vanishing from the Windows interface, and for good reason: CMD commands are an outdated and mainly unneeded utility from the days of text-based input, but many commands are still useful, and Windows 8 and 10 have introduced new functionality.
We've compiled a list of basic commands that every Windows user should be familiar with.
1. Assoc.
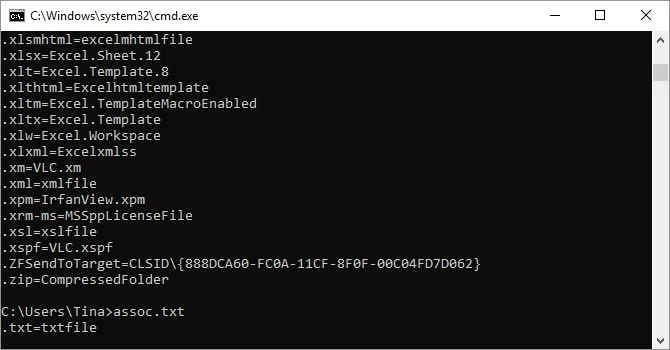
Most files in Windows are connected with a certain program that is set to open them by default, and remembering these connections can be difficult. You may remind yourself by running the command helper and viewing a comprehensive list of file name extensions and application relationships.
To modify file associations, expand the command, such as assoc.txt=. This will change the file association for text files to the program entered after the equals sign. The assoc command displays both the extension and program names, allowing you to use this command appropriately.
Windows 10 has a more user-friendly interface that also allows you to alter file type associations on the fly. Navigate to Settings (Windows + I) > Apps > Default apps, and select the default program based on file type.
2. Cipher.

Deleting files from a mechanical hard disk does not remove them; rather, it identifies the data as no longer accessible and frees up the space they used. The files are recoverable until the system overwrites them with fresh data, which might take some time.
However, the cipher command removes a directory by writing random data to it. To wipe drive C, for example, use the command cipher /w:d, which will delete all empty space on the drive. Because the program does not replace undeleted data, executing it will not remove files that you require.
Other encryption commands can be used, although they are often redundant with BitLocker-enabled Windows editions.
3. DriverQuery
Drivers are still among the most critical pieces of software on your computer, and badly configured or missing drivers may cause a variety of issues, so it's a good idea to have access to a list of what's on your machine, which is precisely what the driverquery command provides. You may expand it to include driverquery -v to obtain further information, such as the directory where the driver is installed.
4. File Compare

This command may be used to identify text differences between two files; it is especially useful for authors and programmers looking for minor changes between two versions of a file. Just type fc followed by the directory location and file name of the two files you wish to compare.
You may further modify the program by using /b to compare just binary output, /c to disregard text case, and /l to compare only ASCII text.
5. Ipconfig
This command sends the IP address that your computer is presently using; however, if you are working behind a router (as most PCs are today), you will receive the router's local network address.
ipconfig is still helpful due to its extensions. ipconfig /release followed by ipconfig /renew can force your Windows machine to seek a new IP address. This is important if your computer claims to be unavailable. You can also use ipconfig /flushdns to refresh your DNS address. These instructions are useful if the Windows Network Troubleshooter is clogged, which it occasionally is.
6. Netstat
Entering the command netstat -an will provide a list of currently open ports and their IP addresses, as well as the port's status, such as listening, creating, or shutting.
This is useful when you're attempting to troubleshoot gadgets connected to your computer or when you suspect a Trojan virus has infiltrated your system and are looking for a harmful connection.
7. Ping
Ping can be useful when you need to know whether packets are reaching a certain networked device or not.
Typing ping followed by an IP address or web domain sends a series of test packets to the given address. If they arrive and return, you know the device can interact with your computer; if they don't, you know something is interfering with communication between the device and your computer. This might help you establish whether the problem is due to a misconfiguration or a malfunction in the network hardware.
8. PathPing.
This is a more complex form of ping that is handy when there are numerous routers between your computer and the device being tested. This command, like ping, may be used by entering pathping followed by the IP address; however, unlike ping, pathping additionally provides information about the path the test packets took.
9. Tracert
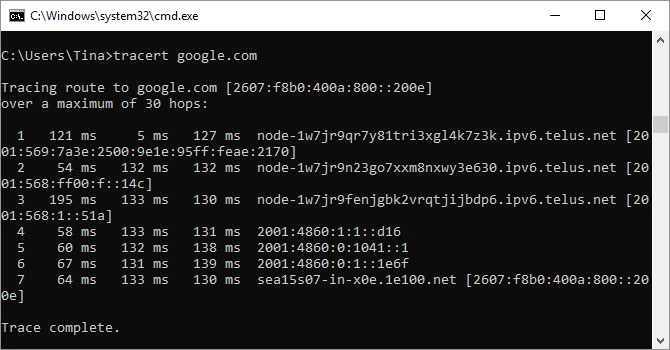
The Tracert command is comparable to the PathPing command. Again, enter tracert, followed by the IP address or domain you wish to trace. You will be informed about each step in the way between your computer and the destination. Tracert, unlike a route, keeps track of how long each hop between servers or devices takes (in milliseconds).
10. Powercfg
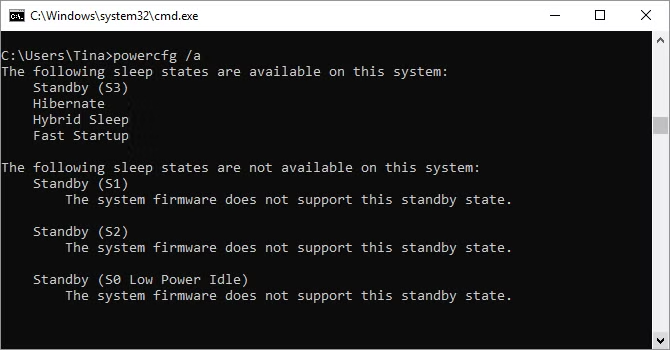
Powercfg is a powerful tool for managing and tracking your computer's power usage. To handle hibernation, use the commands powercfg hibernate on and powercfg hibernate off. You may also use the powercfg /a command to see which power-saving modes are presently available on your machine.
Another handy function is powercfg /devicequery s1_supporte, which lists all of the devices on your computer that support connected standby. When enabled, you may use these devices to pull your computer out of sleep mode remotely. To activate this, pick the device in Device Manager, open its settings, navigate to the Power Management tab, and tick the option labeled Allow this device to wake the computer.
Powercfg /lastwake will show you which device roused your computer from sleep; use this command to troubleshoot your machine if it appears to be waking up from sleep at random.
You may use the powercfg /energy command to get a full report on your computer's power usage. When the command is done, the report is saved in the chosen directory. This report will alert you to any system issues that may be boosting power usage, such as devices that prevent certain sleep modes or are not properly configured to respond to your power management settings.
In Windows 8, powercfg /batteryreport offers a thorough analysis of battery utilization if available. The report is normally included in your Windows user manual and includes information on the time and duration of charge and discharge cycles, average battery life, and estimated battery capacity.
11. Shutdown.
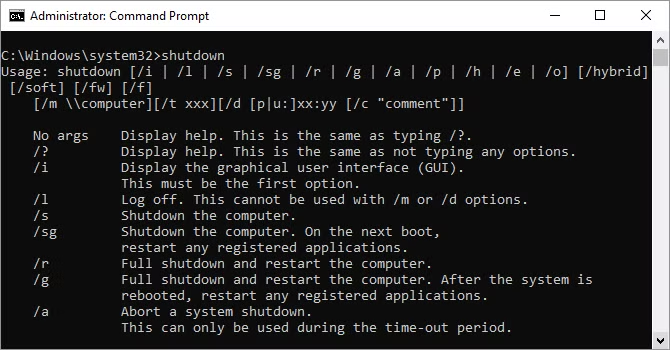
Windows 8 introduces the shutdown command to shut down your machine.
This is obviously redundant with the already easily accessible shutdown button, but it is not redundant with the shutdown /r /o command, which restarts your computer and launches the Advanced Startup Options menu, where you can access Safe Mode and Windows Recovery utilities, which is useful if you need to restart your computer for troubleshooting.
12. SystemInfo
This will offer you a full overview of your computer's settings, including the operating system and hardware. For example, you may search for the original Windows installation date, last boot time, BIOS version, total and available RAM, installed hotfixes, network card settings, and other information.
To obtain remote information for a computer on your local network, use systeminfo /s followed by the computer's hostname. This may necessitate adding syntax components for the domain, username, and password, such as this:
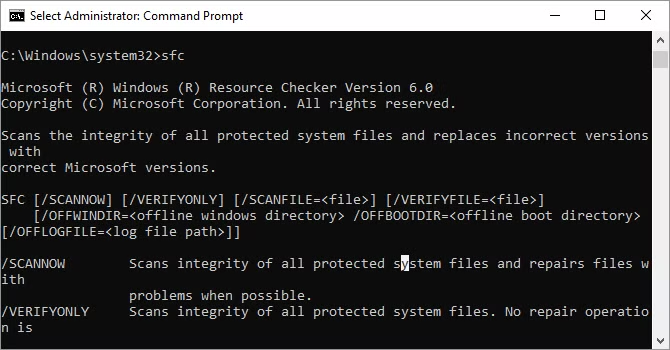
13. System File Checker

System File Checker is an automatic scanning and repair utility for Windows system files.
You'll need to run a command prompt with administrator privileges and enter the sfc /scannow command. If SFC finds any corrupt or missing files, it will automatically replace them using the cached copies that Windows keeps for this purpose only. On older laptops, this can take up to half an hour.
14. Task List
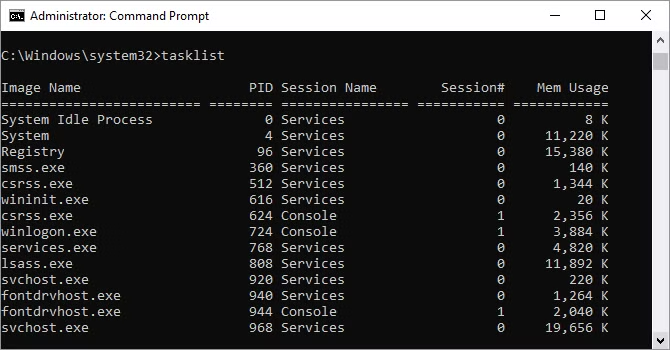
You may use TaskList to display the current list of all running tasks on your computer, and while it is relatively similar to Task Manager, it can occasionally locate activities that are hidden from view in that program.
There are also a variety of modifiers: Tasklist -svc displays the services connected with each job, Tasklist -v provides more information about each task, and Tasklist -m locates DLL files associated with current tasks. These commands are important for performing advanced troubleshooting.
15. Taskkill.
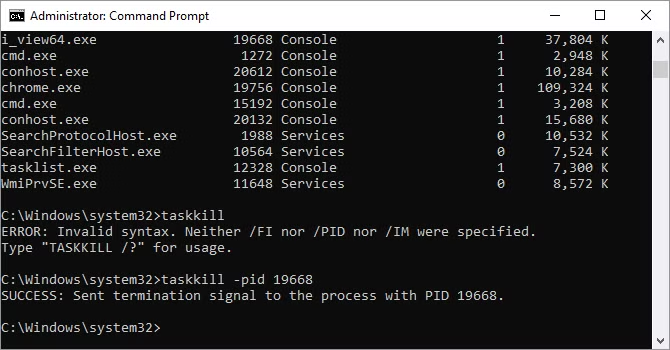
Tasks in Tasklist and Command Prompt are identified by an executable ID and a process (four- or five-digit number), and you may force stop a program by typing taskkill -im followed by the executable name or taskkill -pid followed by the process ID. Again, this is redundant with Task Manager, but it may be used to terminate unresponsive or hidden applications.
16. Chkdsk.
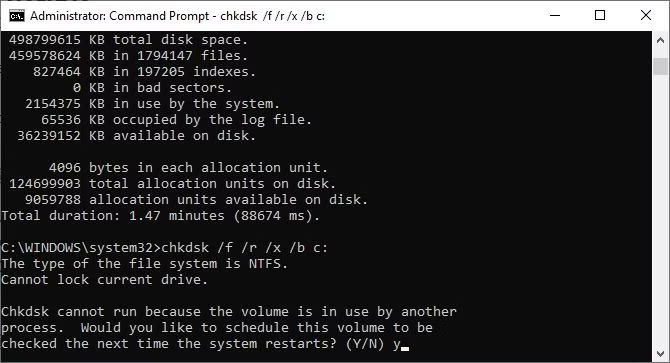
When Windows detects faulty sectors, missing clusters, or other logical or physical defects on your local disk, it immediately marks it for a chkdsk diagnostic check.
If you suspect a hard disk failure, run the scan manually. The fundamental command is chkdsk c:, which scans the C: disk without restarting the computer. When you add options like /f, /r, /x, or /b, as in chkdsk /f /r /x /bc:, chkdsk will rectify problems, recover data, unmount the disk, or remove the list of faulty sectors. These actions need a reboot and can only be performed with Windows switched off.
If you notice chkdsk running at startup, let it do its work.
17. Scheduled tasks
Schtasks gives your Command Prompt access to the Task Scheduler, one of Windows' many underappreciated administrative features. While the GUI may be used to handle scheduled tasks, the Command Prompt allows you to copy and paste complicated instructions to configure several comparable jobs without having to navigate through different choices. Finally, sticking with the fundamental memory settings makes it much easier to use.
Windows 8 only: Recovery image.
Almost all Windows 8/8.1 laptops come preloaded with a recovery image, but it may contain bloatware that you don't want to reinstall. After uninstalling the program, use the recimg command to make a fresh image. Entering this command results in a full description of how to use it.
To use the recimg command, you must have administrative capabilities, and you can only view the custom recovery image made using the Windows 8 Refresh feature.
In Windows 10, the system recovery process has altered. Windows 10 computers no longer include a recovery sector, so backing up your data is more vital than ever.

