The right way to configure and customise Kali Linux settings
Penetration assessments assist decide whether or not vulnerabilities and weaknesses are current in company techniques. An array of pen testing instruments can be found, together with the Kali Linux distribution, which offers every thing an moral hacker must successfully take a look at an organization's techniques.
In Mastering Kali Linux for Superior Penetration Testing, creator and safety practitioner Vijay Kumar Velu offers in-depth directions on learn how to take a look at a community with Kali Linux. Readers will learn to choose the most effective instruments from the distribution to compromise safety, whereas remaining undetected by companies or customers.
For these starting out with Kali Linux, comply with together with the excerpt from Chapter 1 of Mastering Kali Linux to learn to set up and customise Kali Linux settings for the primary time. Obtain a PDF of Chapter 1 here.
Try a Q&A the place Velu defined how pen testers of all expertise ranges can use his guide, why Kali Linux is price utilizing for offensive safety and extra.
Organizing Kali Linux
Set up is only the start; organizing Kali Linux is an important subsequent step. On this part, we'll discover the alternative ways during which our Kali Linux could be organized by customization.
Configuring and customizing Kali Linux
Kali is a framework that's used to carry out penetration testing. The tester, nonetheless, ought to by no means really feel tied to the instruments which were put in by default, or by the appear and feel of the Kali desktop. By customizing Kali, a tester can improve the safety of consumer information that's being collected and make it simpler to carry out a penetration take a look at. Frequent customization choices that may be made in Kali embrace the next:
Mastering
Kali Linux for Superior
Penetration Testing right here.
- Resetting the Kali password
- Including a non-root person
- Configuring community companies and safe communications
- Adjusting community proxy settings
- Accessing the safe shell
- Dashing up Kali operations
- Sharing folders with Microsoft Home windows
- Creating encrypted folders
Allow us to now take an extra take a look at these choices.
Resetting the default password
If you happen to downloaded the preconfigured VMware or VirtualBox picture, the default username and password to entry Kali Linux is kali. It's endorsed to alter the default password; to take action, run the next command within the Kali Linux terminal:

You'll then be prompted to enter a brand new password, after which to substantiate it.
Configuring community companies and safe communications
Step one to make sure that we're capable of entry the interior community is to guarantee that it has connectivity to both a wired or wi-fi community to assist updates and communications. You could must get hold of an IP tackle by Dynamic Host Configuration Protocol (DHCP) by appending a community configuration file and including an Ethernet adapter to it, within the type of the next instructions from the Kali Linux terminal:

As soon as the community configuration file is appended, it is best to have the ability to deliver up the ifup script to routinely assign the IP tackle, as displayed in Determine 1.28:
Determine 1.28: Profitable project of an IP tackle by DHCP utilizing the ifup script
Within the case of a static IP, you possibly can append the identical community configuration file with the next strains and rapidly arrange a static IP to your model of Kali Linux:
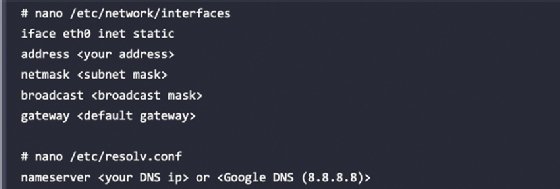
By default, Kali begins with the DHCP service enabled. Doing so publicizes the brand new IP tackle to the community, which can alert directors to the presence of the tester. For some take a look at circumstances, this is probably not a difficulty, and it might be advantageous to have sure companies begin routinely throughout boot-up. This may be achieved by coming into the next instructions:

Kali installs with community companies that may be began or stopped as required, together with DHCP, HTTP, SSH, TFTP, and the VNC server. These companies are normally invoked from the command line; nonetheless, some are accessible from the Kali menu.
Adjusting community proxy settings
Customers positioned behind an authenticated or unauthenticated proxy connection should modify the bash.bashrc and apt.conf information. Each information are positioned within the /and many others/ listing. Edit the bash.bashrc file, as the next exhibits, utilizing a textual content editor so as to add the next strains to the underside of the bash.bashrc file:
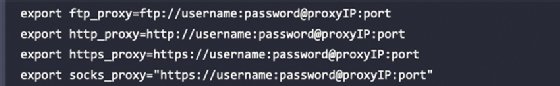
Substitute proxyIP and port along with your proxy IP tackle and port quantity, respectively, and exchange the username and password along with your authentication username and password. If there is not any must authenticate, write solely the half following the @ image. Save and shut the file.
Accessing the safe shell remotely
To attenuate detection by a goal community throughout testing, Kali doesn't allow any exterior listening community companies. Some companies, equivalent to SSH, are already put in. Nevertheless, they should be enabled prior to make use of. Kali comes preconfigured with default SSH keys. Earlier than beginning the SSH service, it's a good suggestion to disable the default keys and generate a singular keyset to be used, as the next code exhibits. Transfer the default SSH keys to a backup folder, after which generate a brand new SSH keyset utilizing the next command:
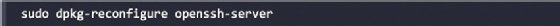
To substantiate the SSH service is working, you possibly can confirm this by utilizing the command sudo service ssh standing.
Word that with the default configuration of SSH, root login can be disabled. If you happen to require entry with the basis account, you will have to edit /and many others/ssh/sshd_config and set PermitRootLogin to sure, save, after which exit. Lastly, from any system on the identical community, it is best to have the ability to entry the SSH service and make the most of Kali Linux. On this instance, we use PuTTY, which is a free and transportable SSH consumer for Home windows. Now it is best to have the ability to entry Kali Linux from one other machine, settle for the SSH certificates, and enter your credentials.
Dashing up Kali operations
A number of instruments can be utilized to optimize and pace up Kali operations:
- When utilizing a VM, set up its software program drive bundle, both Visitor Additions (VirtualBox) or VMware Instruments (VMware).
Word: We've to make sure that we run apt-get replace earlier than the set up.
- When making a VM, choose a hard and fast disk dimension as an alternative of 1 that's dynamically allotted. It's sooner so as to add information to a hard and fast disk, and there may be much less file fragmentation.
- By default, Kali doesn't present all functions which can be current within the startup menu. Every utility that's put in throughout the boot-up course of slows the system information and will influence reminiscence utilization and system efficiency. This may be carried out by the next instructions within the terminal:
- To checklist all of the startup companies at bootup, kind sudo systemctl list-unit-files --type=service within the terminal and you may select to disable the undesirable companies by working sudo systemctl disable --now
- Lastly, you possibly can checklist the enabled companies by working sudo systemctl list-unit-files --type=service --state=enabled --all within the terminal
Sharing folders with the host working system
The Kali toolset has the pliability to share outcomes with functions residing on completely different working techniques, particularly Microsoft Home windows. The simplest option to share information is to create a folder that's accessible from the host working system in addition to the Kali Linux VM visitor. When information is positioned in a shared folder from both the host or the VM, it's instantly accessible by way of the shared folder to all techniques that entry that shared folder. To create a shared folder, carry out the next steps:
- Create a folder on the host working system. On this instance, will probably be referred to as kali_Share.
- Proper-click on the folder and choose the Sharing From this menu, choose Share.
- Be certain that the file is shared with Everybody and that Permission Degree for this share is about to Learn/Write.
- If you have not already achieved so, set up the VMware instruments/Digital Field Visitor additions onto Kali Linux, respectively.
- When the set up is full, go to the VMware participant menu and choose Handle and click on on Digital Machine Settings. Discover the menu that permits Shared Folders and choose All the time Enabled.
- Within the case of Oracle VirtualBox, choose the VM and go to Settings and choose Shared Folders, as proven in Determine 1.29:
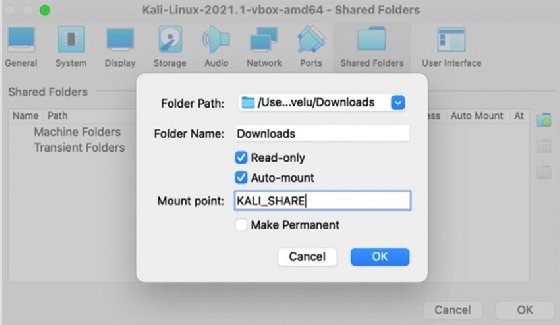
Determine 1.29: Mounting a shared drive from the unique working system to the visitor working system
Word: Please notice that older variations of VMware Participant use a distinct menu.
- Now the folder ought to be routinely mounted to the /media/ folder, as proven in Determine 1.30:
Determine 1.30: Profitable mounting of the shared drive to the Kali Linux VM - All the pieces positioned within the folder can be accessible within the folder of the identical identify on the host working system, and vice versa.
The shared folder, which is able to comprise delicate information from a penetration take a look at, should be encrypted to guard the consumer's community and scale back the tester's legal responsibility ought to the info ever be misplaced or stolen.
Editor's notice: This text was up to date to enhance the reader expertise.
Concerning the guide creator: Vijay Kumar Velu, creator of 4 IT safety books, holds a variety of safety certifications and is licensed penetration tester with 20 years of business expertise.


